A popular jQuery upload plugin used .htaccess for security control but the default behaviour in Apache changed 8 years ago (v2.3.9) so attackers have been able to upload payloads using the plugin ever since.
Luckily it’s only the 2nd biggest jQuery repo on GitHub that’s been forked 7,834 times!
But wait, it gets better!
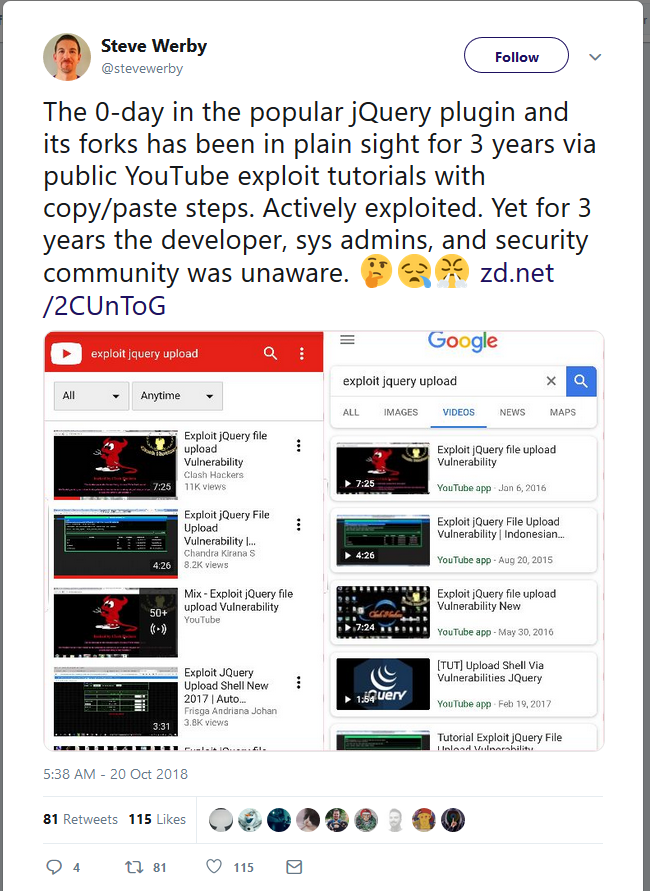 https://twitter.com/stevewerby/status/1053354746658967552
https://twitter.com/stevewerby/status/1053354746658967552
Here’s the full write up from Larry Cashdollar - Having The Security Rug Pulled Out From Under You
UPDATE 23/10/2018
Simple fix proposed in this git commit.
Insights from the author replying in HN thread (source)
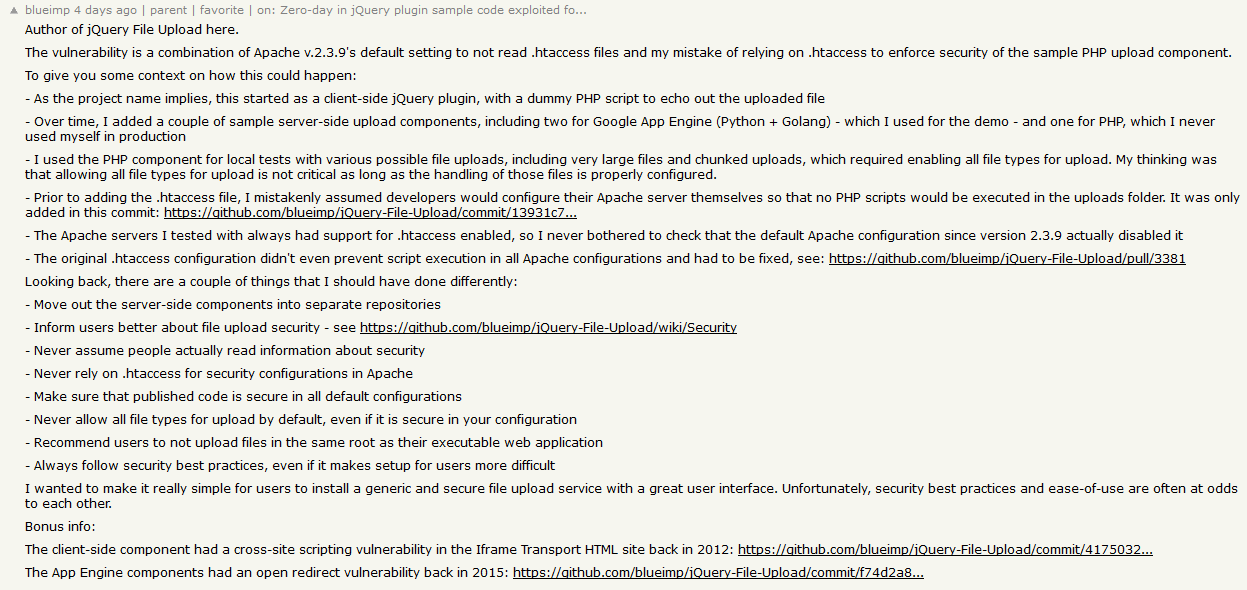
Always assume lusers will ignore documentation and copy example code verbatim.
No better time to review the abusing .htaccess workshop from Eldar Marcussen at CONFidence 2018, Krakow